Table of Contents
Introduction
One essential tool to master as a system administrator is SSH.
SSH, or Secure Shell, is a protocol used to securely log onto remote server. It is the most common way to access remote Linux servers.
In this guide, we will discuss how to use SSH to connect to a remote system. By the end of this guide, you’ll be more confident in using SSH to make your computer talks safe and secure when dealing with those remote servers.
What is SSH?
SSH, or Secure Shell, constitutes a cryptographic network protocol designed to enable secure communication between two systems over networks that may not be secure. This protocol is widely employed for remote access to servers and the secure transmission of files between computers. In essence, SSH acts as a secure conduit, establishing a confidential channel for communication in scenarios where the network may pose security risks. This technology is instrumental for professionals seeking a reliable and secure method of managing servers and transferring sensitive data across computers in a controlled and protected manner. ssh runs at TCP/IP port 22.

The basic syntax for using the SSH command is as follows:
ssh [username]@[hostname or IP address]
Replace [username] with your remote server username, and [hostname or IP address] with the server’s hostname or IP address.
Secure Shell capabilities
Functions that SSH enables include the following:
- secure remote access to SSH-enabled network systems or devices for users, as well as automated processes
- secure and interactive file transfer sessions
- automated and secured file transfers
- secure issuance of commands on remote devices or systems and
- secure management of network infrastructure components.
SSH can be used interactively to enable terminal sessions and should be used instead of the less secure Telnet program. SSH is also commonly used in scripts and other software to enable programs and systems to remotely and securely access data and other resources.
Prerequisites
Before delving into the world of SSH, it’s essential to ensure that certain prerequisites are in place. Here’s a checklist to guarantee a smooth connection:
- Remote Computer Status:
- Make sure the remote computer is turned on and has an active network connection. SSH relies on network connectivity, and the remote server needs to be accessible.
- Identification Information:
- Obtain the IP address or the name of the remote machine. This information is crucial for directing your SSH connection to the correct server.
- Permission to Access:
- Ensure that you have the necessary permissions to access the remote computer. This typically involves having a valid username and password for the remote server.
- Firewall Settings:
- Check the firewall settings on both your local machine and the remote server. SSH connections use a specific port (usually port 22), so it’s crucial to ensure that your firewall allows SSH traffic. Adjustments may be required to permit secure communication.
Install SSH Component on Linux
Setting up SSH on Linux may be necessary, as some distributions don’t come with it pre-installed. Installing OpenSSH, a widely used SSH implementation, or opting for a graphical user interface (GUI) solution like the PuTTY client for Ubuntu can address this. Here’s a step-by-step guide on installing and configuring OpenSSH on both the client and server sides:
Installing it on Both Client and Server
For Debian/Ubuntu-based Systems, open the terminal and run:
sudo apt install openssh-client openssh-server
For Red Hat-based systems like CentOS or Fedora, use either of the following commands:
sudo dnf install openssh-clients openssh-server
or
sudo yum install openssh-clients openssh-server
How to Use SSH to Connect to a Remote Server in Linux
In this example we access Ubuntu or Red hat Linux machine via the Windows command prompt using `ssh`
For example: If our IP address is “103.877.904.245” and username is “posh”
Syntax to use ssh to connect to a remote server:
ssh posh@103.877.904.245
Add your username in place of “posh” and add your IP address in place of “103.877.904.245”
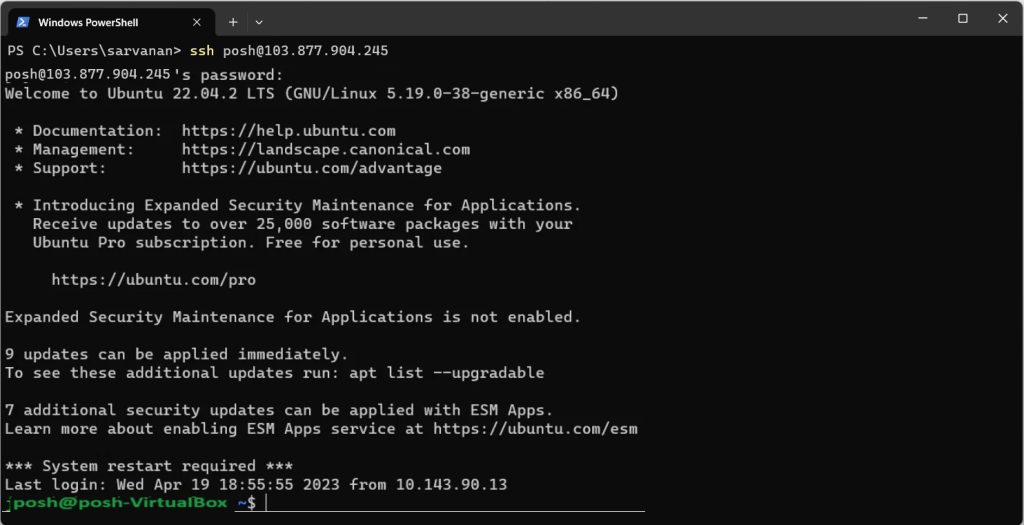
Command consists of 3 different parts:
- ssh command instructs the system to establish an encrypted secure connection with the host machine.
- user_name represents the account that is being accessed on the host.
- host refers to the machine which can be a computer or a router that is being accessed. It can be an IP address (e.g., 103.877.904.245) or domain e.g., www.domainname.com).
Note: After logging into the host computer, commands will work as if they were written directly to the host terminal. Using a public-private key pair or SSH key pair to login into the remote host is more secure as compared to using passwords.




